
The new 5G Core network (5GC) is completely based on what is called a Service-Based Architecture (SBA), which implements IT network principles and a cloud-native design approach. Thus, 5GC network functions (NFs) are refactored into individual micro-services coming together to automatically discover each other, and utilize the services offered by each other. With this refactoring, NFs become composed of a multitude of services, each of which might have many instances. With the increasing number of such micro-services, the complexity of service-to-service communications is further increased. And to overcome this challenge, 3GPP has drawn on IT experiences and adopted the “service discovery” concept, one of the NRF‘s tasks.
In this blog, we will describe the NRF (Network Repository Function), its benefits and all the services that offers.
SBA Challenge
To enhance the flexibility and scalability of the network, 3GPP has adopted the SBA approach. With this new architecture, the core network is decomposed into well-defined, standardized network functions that communicate with each other using standardized interfaces and protocols. 4G core network elements are decomposed into individual services called Network Functions (NFs) and new NFs were added to meet the needs of the new 5G use cases, like NRF, NSSF etc… (see figure 1)

The table below outlines the decomposition of some EPC network elements:

SBA design also consists in reorganizing network elements into NF consumers and NF producers that are coming together to automatically discover each other, and utilize the services offered by each other. Moreover, 5GC NFs will be implemented using the micro-service architecture, which means that each NF will be formed by a combination of micro-services running with dynamic changes. Each NF is divided into several self-contained, self-managed and reusable network function services (NFSs) which can operate independently without relying on each other.
This approach will certainly enhance the flexibility, scalability and efficiency of the new 5G core network. However, with the increasing number and dynamic/volatile nature of such micro-services, the complexity of the network architecture is further increased. Which lead to the need for an automatic mechanism that allows services to locate and communicate with other services without the need for a complex and static configuration. These challenges are the key reasons behind the 3GPP adopting of IT service discovery concept and the introduction of a new NF called NRF.
NRF services
In previous generations of mobile core networks (2G, 3G and 4G), if a new function is introduced or an existing network element is expanded, the operator needs to reconfigure all the existing networks elements with the information needed to address the newly added equipment. In 5G however, this static configuration does not fit the dynamic environment of the SBA architecture, which leads to the introduction of the NRF. The NRF removes the need for network configuration every time a new NF is added/removed from the network, or every time NF capacity is expanded.
The NRF is a central registry, holding information about every NF, which can then be shared with any NF, when required. It can be viewed as an evolution of the DNS in EPC networks with enhanced capabilities.
In practice, when you bring a new NF or expand an existing one, this new NF instance only need to interact with the NRF in order to register its profile and discover all the NFs composing the network.

To maintain its database and to have a continually up-to-date topology view, the NRF allows NFs to register/deregister itself, its supported services and to update their status. Additionally, the NRF allows NF instances to subscribe to status updates of other peers. Any registration, deregistration or profile change of an NF instance should be notified to other NFs which result in keeping NF local cache up-to-date and thus minimizing the number of NRF queries.
The following table shows the NRF services and service operations:

NF discovery
Service discovery is the process of automatically finding what instances of a service fulfil a given request. Upon receipt of the discovery message from the NF consumer, the NRF checks its own database and selects a list of available service producers from the registered NFs based on different parameters specified by the consumer NF.
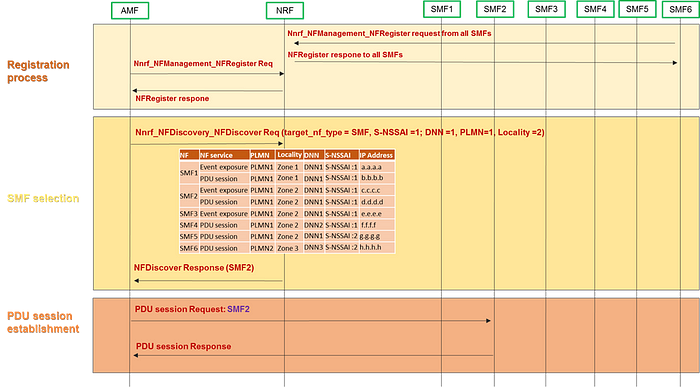
The call flow above is an example to illustrate the SMF selection process:
1. All the NFs (AMF and SMFs) need to register their profiles in the NRF. The NF profile contains: supported services, PLMN, IP address, DNN, S-NSSAI …
2. The consumer AMF initiates a discovery request to the NRF, searching for an available SMF fitting the requirements (NF service= PDU session; S-NSSAI =1; DNN =1, PLMN=1, Locality =2)
3. The NRF checks its own database and selects an SMF that fits the AMF requirements. In our case, the only SMF matching the discovery criteria is SMF2. Which means that the whole selection process is done by the NRF.
N.B: When the NRF replies with a list of available NF producers, the NF consumer should handle the selection or delegates this process to the SCP (if one exists). For more details about this case, you can refer to my previous post about “C or D model”.
4. The AMF send then a PDU session request to the selected SMF to establish a session.
NF authorization
The 5GC introduces the notion that an NF can discover all other NFs by consulting the NRF. Therefore, and for security reasons, NF consumers have to be authorized before initiating a service request. Thus an NF producer defines access authorization policies (based on NF type, PLMN, S-NSSAI…) to determine the NF consumers that can access it. The policies can be sent to the NRF during the registration/profile update processes or can be configured directly on the NRF. This kind of authorization is called static authorization (like authorization mechanisms used in 3G/4G) and it can be implemented when token-based authorization is not used.
Token-based authorization
To secure intra-domain communications between NFs, 3GPP has introduced the Token-based authorization, a new concept based on OAuth2.0 framework (as specified in RFC 6749) where the NRF plays the role of “Authorization server” to restrict unauthorized NF consumers to access the services provided by the NF producers.
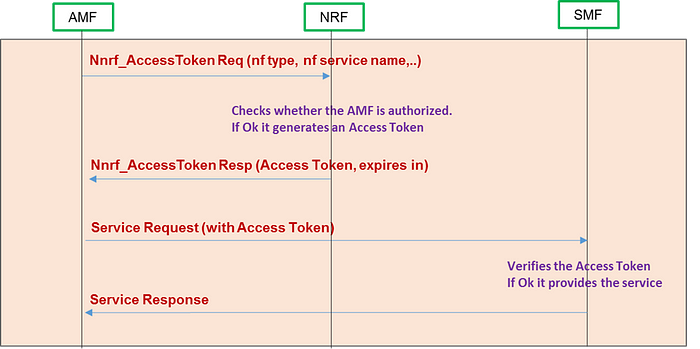
When an NF sends a discovery request, it requests an access token from an NRF. The NRF then issues an access token with a validity period.
After receiving the service request from the consumer (OAuth client), the NF producer in “Resource server” role shall validate the access token, its expiry and its access scope before authorizing the access to the provided services.
N.B:
· Token-based authorization is performed when a NF consumer invokes a NF producer for the first time, access token expires or there is a change in the requested service.
· Token-based authorization is optional in case mTLS is used. However, with the complexity that TLS brings, many operators are opting for token-based authorization (application layer security) as a security solution for intra NF communications.
Selection & Load Balancing
The NRF, as a centralized repository for all the 5G core network functions, maintains an updated record of NF status and their profiles. Among the attributes that compose a NF profile, are Capacity, Priority and Load. These parameters, if present, can help in performing NF selection and load balancing:
· NF priority: lower values indicate a higher priority.
· NF Capacity: static information expressed as a weight relative to other NF instances of the same type.
· NF Load: dynamic load information (0 to 100); indicates the current load percentage of the NF.
The call flow below illustrates the role of the NRF in providing selection & load balancing:

· Upon receiving a service discovery request from the AMF, the NRF selects available UDM instances (UDM1, UDM2, UDM3 and UDM4) based on SUPI ranges and returns the service discovery result. The NRF response includes priority, capacity and load of each UDM instance.
· The AMF will use the information priority, capacity and load to select the appropriate UDM instances (UDM3 is not selected because of its load and UDM4 because of its priority).
· The AMF calculates the percentage based on the free capacities (40% and 60% in our case) and send the requests to UDM1/UDM2.
N.B: when an SCP is used, NFs will be relieved from managing all those selection and load balancing mechanisms.
NRF deployment
The NRF is a function that can be deployed standalone or can be collocated with other network functions. The table below shows NRF implementation per vendor:

As you can see from the table above, most of the vendors are implementing the NRF function as a standalone solution combined with the NSSF function. However, 3GPP in their TS 23.501 recommanded to collocate the NRF with the SCP when model D is adopted.
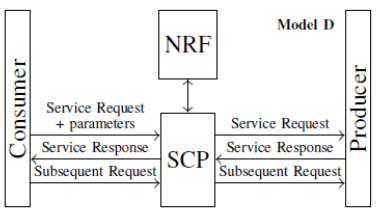
3GPP recommendation is mainly justified by the volume of the traffic exchanged between NRF and SCP. In model D as you know, communications between NF consumers and NF producers are indirect and all the NRF traffic (service discovery, authorization, selection and load balancing) goes through the SCP (see figure 6). Thus, when NRF and SCP work together, they can enable more optimized NF selection/load balancing and a better-secured NF-NF communication.
Summary
3GPP introduces the NRF to deal with SBA challenges and enhance the autonomy of networks. In small deployments, NFs can be configured manually and can communicate by creating static links among themselves. However, in medium- and large-sized 5G networks, this static configuration become unmanageable.
As a discovery solution, the NRF automate the network so that each new NF instance can be plug-and-play. NFs can be upgraded; expanded or removed independently with minimal impact on each other, which reduces operational costs and time-to-market of new solutions.
Given its role in the 5G core, the NRF has a complete view of the topology, capacity and performance of the network. Therefore, it can help to centralize selections decisions and to better control the overall load balancing in the network. The NRF can also enhance the security of the network by implementing the NF authorization mechanism.
To conclude, the NRF allow operators to get the most of the new 5G architecture in terms of flexibility, efficiency and automation.
References:
-3GPP TS 29.510
-3GPP TS 23.502
-3GPP TS 33.501
